by Lynnette Reese, contributing editor
Most of us assume that security comes from the operating system or application software. However, firmware is also at risk, including anything that barely hovers over the physical layer (silicon) in the chip. Embedded security is especially important in blocking seemingly innocuous pathways for hacking, such as in an automotive infotainment center.
Most of us assume that security comes from the operating system or application software. However, the firmware is also at risk, including anything that barely hovers over the physical layer (silicon) in the chip. Booting up a chip means that some hardcoding in the silicon itself is permanent (unless a portion of the chip is FPGA-based). Anything above that permanent coding, which acts like a tiny boot loader, is vulnerable to hacking.
After a chip is powered up, it looks for firmware in memory, usually ROM. That firmware provides boot management services. However, for decades firmware so low on the stack hasn’t been armored with security measures like requiring it to be cryptographically authenticated by the tiny silicon-based boot loader. Firmware further up the stack for system management can be vulnerable without any checks for authenticity, too. If the firmware is designed without any consideration for security, then hackers can subvert the fundamental, root-functioning operations to do their bidding without detection by changing the firmware. Any subsequent security checks from anything higher in the stack, such as the operating system or application programs, could be orchestrated to do what the hacker wants. Therefore, it’s imperative that security starts at the physical layer as a function provided by the chip manufacturer.
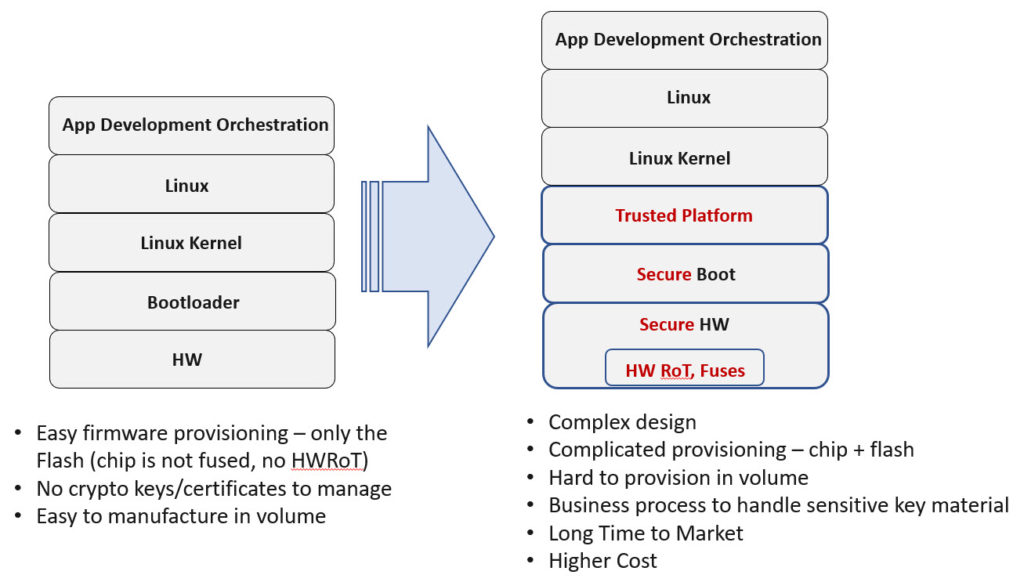
The depth of the process for securing everything from silicon to product design, development, volume product manufacturing, and throughout the product’s lifecycle (including firmware and software updates) is a tremendous learning curve. Companies like NXP offer a means to secure embedded products starting in the silicon. However, seamlessly incorporating and coordinating the embedded security throughout the supply chain is a daunting project with a steep learning curve.
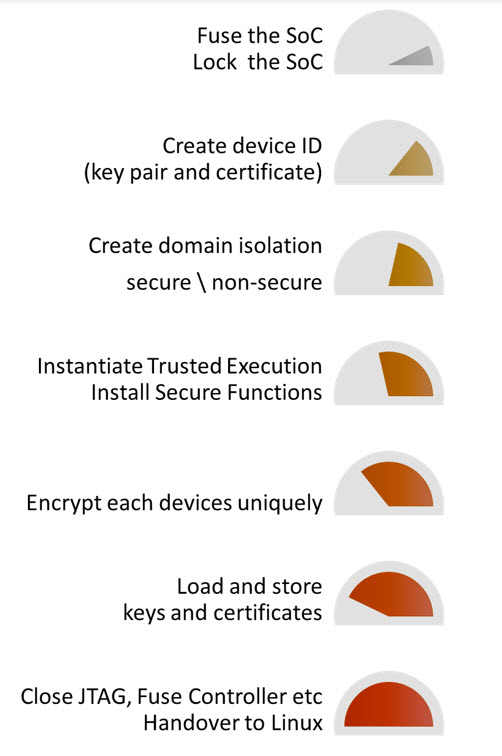
The importance of a secure supply chain
Even securing an automotive infotainment system is vital, since it’s possible to hack any of a hundred or more control units positioned in different systems throughout modern vehicles today. NXP provides the security at the silicon layer in NXP’s i.MX 8 and i.MX 8M application processors. NXP’s i.MX 8M high-performance chips feature up to four Arm® Cortex®-M4 and Cortex®-A53 cores designed to meet the requirements of an enhanced multimedia user experience for smart applications. According to an NXP fact sheet, “Built with advanced media processing, secure domain partitioning and innovative vision processing, the i.MX 8 applications processor family will revolutionize multiple display automotive applications, industrial systems, vision, HMI, and single-board computers.”
It’s critical that integrated chips, passives, power supplies, connectors, and all electronic devices be authentic. Counterfeit products can cause anything from catastrophic failure to a shorter product life that results in poor product reviews. Counterfeit products can be extremely difficult to spot. Besides purchasing individual components directly from the manufacturer, purchasing components from an authorized distributor with anti-counterfeit parts risk mitigation measures in place, such as Mouser Electronics, is imperative.
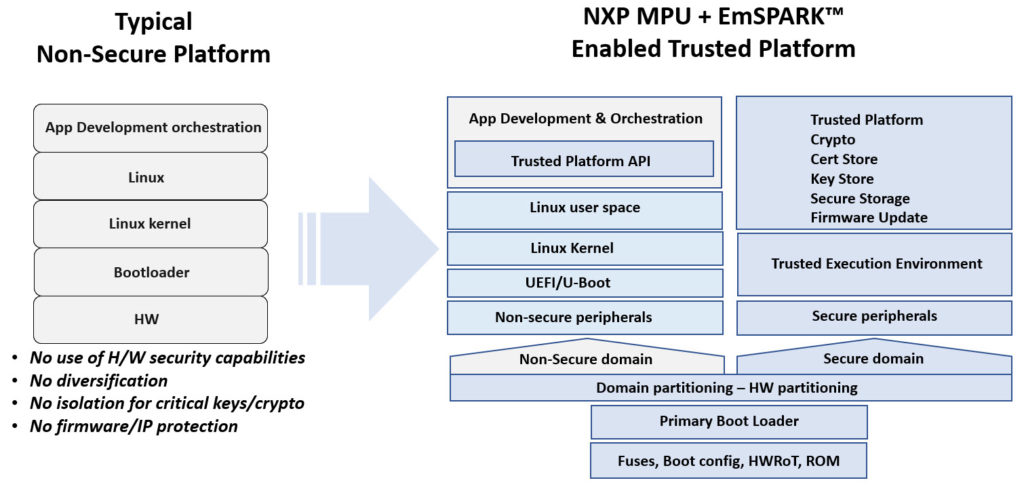
Starting with secure silicon is important, but how do you ensure secure boot managers, firmware, application delivery during manufacturing, and subsequent firmware updates for vehicles already in service? One answer is to do it yourself, but how do you know what you don’t know? There are some companies that have been working for years on embedded security with a wholistic, viewpoint. For instance, Sequitur Labs has a vetted cradle-to-grave security solution for NXP’s i.MX 8 and 8M families of application processors. Sequitur Labs’ EmSPARK Security Suite™ can ensure an easy security process because they’ve abstracted the tedious process from end-to-end. Using NXP’s Trust Architecture, development tools can provide an extended secure boot process bound to a hardware root of trust.
Establishing a hardware isolated secure domain (enclave) can also extend through protecting firmware in volume manufacturing, implementing the necessary “plumbing” to ensure that any updates to processors can only be accomplished by authorized entities. If the production of an embedded device is farmed out to external assemblers or manufacturers, the external company can only load encrypted software, which locks them out from accessing any intellectual property. Not all embedded security tools go this far. For example, with tools like the EmSPARK Security Suite working with NXP’s i.MX8, only software with the proper security key that you create can get unlocked by the chip just after powering up. Any updates required during the lifetime of the product – for example, a car infotainment center – would be enabled; but only if the car’s NXP infotainment processor authenticates the update as genuine by using the keys that were originally generated by the Sequitur Labs’ tools suite. Even the update process is flexible, however, and one can delegate authority. For example, if an OEM creates a product for a customer, but the customer wants to manage the devices themselves, the customer can own the secure update process.
It’s unfortunate that the digital gifts that technology has bestowed upon mankind are vulnerable to the criminal intentions of others. Technology has grown tremendously by building on the shoulders of giants. Engineers, scientists, developers, hobbyists, and others who use technology to create marvelous things that enhance human productivity and create joy in everyday living must now consider securing intellectual property, life, and limb. It’s good to know that NXP and their ecosystem partners like Sequitur Labs work hard in safekeeping the creative process for others.



Growing IoT applications is increasing the demand for IoT security and with the inclusion of payments functionality in wearables the embedded security market is expected to witness significant growth.