Even the best coding practices are likely to result in vehicles infected with 10,000 software bugs. Simulated attacks can sniff out vulnerabilities before the car hits the road.
Hwee Yng Yeo, | Keysight Technologies
The era of the connected car, and a growing concern over cybersecurity threats, is here. Safeguarding the connected car is no easy task. According to Code Complete (by Steve McConnell; Cob and Mills, 1990), even the best coding practices produce one coding error per 10,000 lines of code. With about 100,000,000 lines of code in a modern high-end car, this works out to about 10,000 software bugs onboard!

Also worrying: According to Upstream Security’s Global Automotive Cybersecurity Report 2020, the number of reported automotive cyber-security incidents almost doubled between 2018 and 2019. The study analyzed 367 automotive cyber-attack incidents since 2010, 155 of which were from 2019. These latest figures equate to a 94% year-on-year growth.
The more dramatic hacks and threats to personal safety often make headlines, such as white-hat carjacking with packet codes sent over the internet. This exposed vulnerability heightens the fear that hackers can hijack autonomous vehicles miles way, with helpless passengers onboard. But according to the financial research firm Fortunly, 71% of all data breaches are financially motivated. Seemingly mundane information such as route preferences, credit card payment records, or the driver’s locations, can fetch high prices from seeking bidders.
A single cyber hack can cost car makers up to $1 billion and a loss of reputation and customer trust. That’s why car makers are considering cybersecurity ratings for cars – the brand or model that sports a five-shield security rating will likely bolster the brand’s value and fetch a premium.
A hacker’s paradise?
Part of the allure of the connected car is the convenience of an internet-on-wheels. But such convenience comes with higher standards for security so the next android package kit (APK) downloaded to your car doesn’t come with Trojan horses that can steal your personal data, or worse, disable your brakes. A closer look at the sub-systems enabling vehicular communication reveals numerous points of vulnerability. Hackers can attempt various incursions ranging from cryptographic attacks at the hardware level to over-the-air (OTA) protocol attacks.
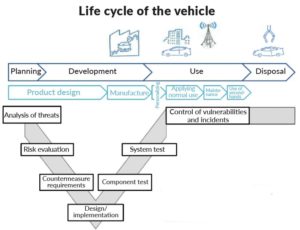
The industry is aware of the need to fortify these at-risk interfaces, but there is no official automotive cybersecurity standard. Car makers and their Tier 1 supply chain develop their own special cybersecurity requirements. These are based on best practices from the SAE J3061 Cybersecurity Guidebook for Cyber-Physical Vehicle Systems, the NIST Risk Management for Automotive Cybersecurity, AUTO-ISAC recommendations, and others.
At the time of this writing, the automotive industry is awaiting the ratification of a new ISO/SAE 21434 standard. It is aimed at securing the systematic development of safe vehicles and maintaining this security throughout the entire vehicle life cycle. The ISO/SAE 21434 standard combines both safety and security. It specifies requirements for cybersecurity risk management regarding engineering for concept, development, production, operation, maintenance, and decommissioning for road vehicle electrical and electronic systems, including their components and interfaces.
Even as the industry awaits official standards, most automotive OEMs and subsystem makers include cybersecurity risk management in their fleet’s product life cycle. There must be security checks at each stage of design verification and functional test validation. Throughout its life on the road, a car remains vulnerable to security threats. This is why sub-systems such as ECUs must be hack-proof, while security systems must protect the car regardless of firmware updates or app downloads throughout its life. Security even extends to protocols that remove sensitive data before the car’s last journey to the scrapyard.
One way automotive design and test engineers try to secure the car is by using a holistic intrusion protection strategy. It combines hardware security validation with software to stress-test potential attack interfaces against a dynamic library of threats. Automotive cybersecurity developers aim to stay steps ahead of hackers, so engineers must constantly update their test plans and run them against a “live” application and threat intelligence (ATI) library. For example, Keysight operates ATI subscription services spanning years of knowledge gained from attack information. Both wireless and wire-line interfaces within the car can be tested to validate safety-critical components such as ECUs, as well as communication systems for advanced driver assistance systems (ADAS), and vehicle-to-everything (V2X) applications.
Cybersecurity pen test
A cybersecurity penetration test architecture may comprise five key components:
- Connectivity gateways – Allow both wired and wireless connections to the various automotive DUTs.
- Test management server – Lets white hat engineers manage their test plans, including scanning for vulnerabilities through various reconnaissance scenarios such as port scanning, fuzz testing, and many more.
- Recon and fuzzing server – The fuzzing plus many other pen test scenarios run on a server. This is where coding errors and other security loopholes are uncovered before cyberattacks get simulated.
- Application & threat intelligence (ATI) library – This stores all captured threats and information. It provides granular application-level visibility and control, geolocation, known-bad IP address blocking, and other threat information.
- Automation – With hundreds of DUTs and thousands of test plans, an intelligent automation platform provides a sanity check for engineers to keep their pen test operations together.

A typical List APK Test plan may not take long to run. But challenges add up quickly. Imagine hundreds or even thousands of test plans, coupled with DUT revisions and software upgrades.
A holistic penetration test platform allows engineers to examine the plethora of cybersecurity loopholes that may put the driver, passenger, and the marque at risk. No single car maker has an exhaustive list of cybersecurity vulnerabilities. That is one reason why car makers are turning to what their IoT counterparts have done – subscribe to secure and dynamic threat intelligence libraries that are available 24×7.

One of the challenges automakers face is the need for a systematic and consistent automotive cybersecurity test strategy across different R&D and production teams. Issues shared among the fraternity include poor test-record management and best practices lost via brain drain, as this growing industry provides career mobility for those with experience and expertise.
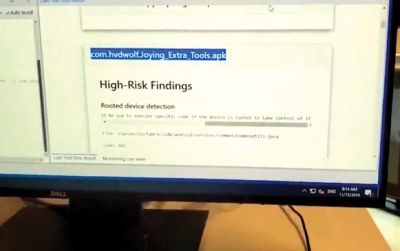
Even as the white hats build up their arsenal of test plans, management teams are rethinking automotive cybersecurity. The industry knows a piecemeal approach to defense is no longer sufficient. Enterprise-level platforms will become increasingly important to help car makers enhance safety and security as the world moves towards autonomous technologies.
Big data from such enterprise-level cybersecurity platforms can have bubble-up benefits for the whole automotive industry. Test engineers can keep track of different test configurations and perform re-tests with design changes, improving productivity and product or services quality. Management can glean insights about threat trends and patterns and formulate better defenses to secure the connected car of the future.




Leave a Reply