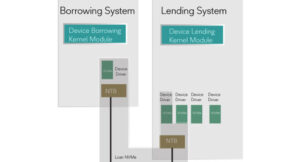
Peripheral Component Interconnect Express (PCIe) is more than just a high-speed serial bus that’s widely used in computers. PCIe is also found in some embedded systems and is a cost-effective, high performance, reliable, low-latency, and low power bus that can rapidly transfer data directly between PCIe-connected devices. PCIe-connected devices are typically CPUs, GPUs, FPGAs, PCIe-connected […]
basics
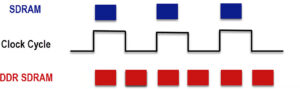
What is DDR (Double Data Rate) memory and SDRAM memory?
DDR SDRAM is a stack of acronyms. Double Data Rate (DDR) Synchronous Dynamic Random Access Memory (SDRAM) is a common type of memory used as RAM for most every modern processor. First on the scene of this stack of acronyms was Dynamic Random-Access Memory (DRAM), introduced in the 1970s. DRAM is not regulated by a […]
Microcontroller power source considerations for Arduino
Powering an Arduino has a little magic to it. It wasn’t obvious to me when I first started working with them, but Arduinos have on-board regulation. Taking advantage of this allows for longer power supply wiring runs by using a higher voltage power supply than the nominal 5V or 3.3V needed by the microcontroller (MCU) […]
8-bits and counting: 8-bit MCUs are still going strong
Microcontroller units (MCUs) never stop evolving; a more functional, featured MCU follows every model. Embedded systems have grown with continually growing MCU technology, yet there are many traditional MCUs that are still selling in high volumes. Atmel 8051 is one of those legendary MCUs which have developed a considerable demand in the market. The Atmel […]
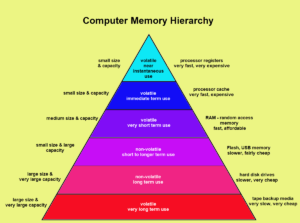
The complexities of cache
Traditionally a cache is a safe place to keep things hidden until you can retrieve them. However, a cache within computer terminology is any storage that is managed to take advantage of location for rapid access. Cache is local memory that exists in the data path between the processor and main memory. A cache will […]
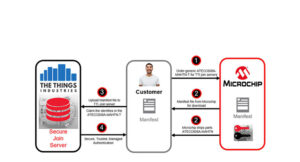
LoRaWAN security design tips: Designing with a stand-alone security chip
With the growth of the Internet of Things, cyber attacks are increasing at an alarming rate (Figure 1). Key provisioning, a process of key generation and device authentication, is a critical part of establishing security. Whoever holds the key will be able to access the payloads, i.e. the valuable data stored in the application server(s). […]
When asked the impossible, ask questions before proceeding
Sometimes a client will ask for the impossible and expect it at low cost. Or worse yet, the sales engineer in your company will win a project on a low bid because he/she thought it could be accomplished in a “creative” (but impossible) way. What if you were tasked with a wirelessly communicating embedded project […]
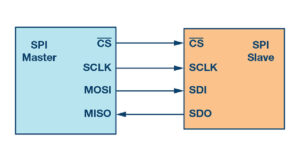
Understanding single-ended and differential communication systems
Do you know the difference between single-ended and differential communication schemes? And when should you use them, which one you should use, and why? Single-ended communications set ups are meant to be used only for short runs or to provide communication between devices on the same Printed Circuit Board (PCB). Single-ended communications will reference the […]
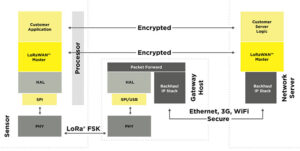
Cybersecurity basics: Server and end device relationship to LoRaWAN network, Part 1
Providing end-to-end security is the ultimate security goal of every wireless network. Each reported successful cyber attack serves as a reminder that achieving security is easier said than done. Let’s first examine the process. Most of us know about using strong passwords and encryption. The most vulnerable security component is key management during device activation […]
Protecting an MCU: Build your own optocoupler
Microcontrollers are widely used for controlling transistors and relays. Transistors and relays are used for actuating or (energizing) equipment with a higher voltage than an MCU can handle. For example, fans, lights, television, door locks, furnaces, and appliances can be automated using an MCU. However, most operate at higher voltages than the voltage tolerances designated […]