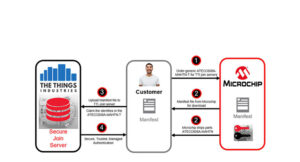
With the growth of the Internet of Things, cyber attacks are increasing at an alarming rate (Figure 1). Key provisioning, a process of key generation and device authentication, is a critical part of establishing security. Whoever holds the key will be able to access the payloads, i.e. the valuable data stored in the application server(s). […]
thethingsindustries
Secure provisioning service builds-in security from inception to life of LoRaWAN device
Just as agile software principles are being adapted for hardware development, so secure provisioning IT practices are finding their way into the semiconductor industry — a move accelerated by the necessity of keeping the increasing number and vulnerability of connected IoT devices. While LoRa technology is sweet spot for low-power connectivity, security remains an area for […]